
About Port Isolation
Port Isolation prevents local switching among ports on a Netvisor ONE switch or on a pair of Netvisor ONE switches configured as a cluster. With Port Isolation, Netvisor ONE disables direct communication with hosts part of same Layer 2 domain connected to isolated ports or to mutually learn the other MAC address. Communication between these hosts occurs through a Layer 3 device. Use this feature to secure bridged east-west traffic through a firewall.
When using this feature on ports within a cluster, you must configure the port-link state association rules between the uplink ports and the downlink isolated ports.
Example Configuration
In a typical scenario, as shown in the Figure 13-1 below, ports 1, 2, and 3 are configured as isolated ports so that the hosts attached to these ports cannot communicate with each other directly, but only through the upstream firewall or router that is connected to port 64.
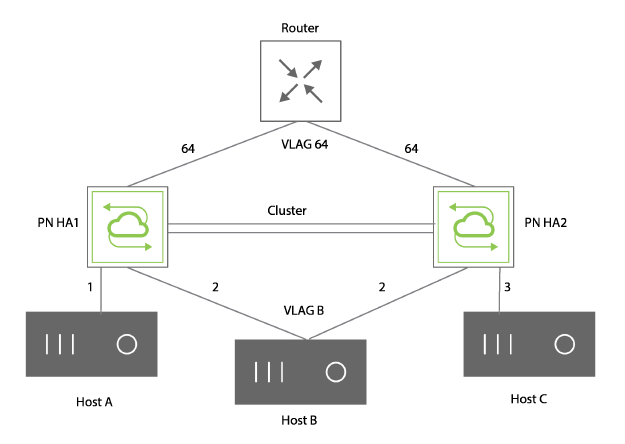
Figure 13-1 - Port Isolation Scenario
As shown in the figure, create the configuration as follows:
PN-HA1
CLI (network-admin@Leaf1) > port-config-modify port 1 no-local-switching
CLI (network-admin@Leaf1) > port-config-modify port 2 no-local switching
PN-HA2
CLI (network-admin@Leaf1) > port-config-modify port 2 no-local-switching
CLI (network-admin@Leaf1) > port-config-modify port 3 no-local-switching
Typically, you configure the upstream router or firewall to perform local proxy ARPs and/or NDP proxy and respond to all ARP requests and/or Neighbor Solicitations coming from isolated hosts.
To avoid interfering with local proxy ARPs and NDP proxy, disable ARP and ND Optimization as follows:
CLI (network-admin@Leaf1) > system-settings-modify no-optimize-arps
CLI (network-admin@Leaf1) > system-settings-modify no-optimize-nd
