
Understanding TACACS+
About TACACS+
Terminal Access Controller Access Control System (TACACS+) is an Authentication, Authorization, and Accounting (AAA) protocol that
provides a centralized database to use for authentication and authorization. This protocol uses a client server approach by which the client queries a server and the server replies with a pass or fail for authentication. The communication between the client and server uses TCP as the transport protocol, and requires a secret key.
Netvisor ONE allows you to configure external TACACS+ servers for authentication, authorization, and accounting of sessions. You can configure any number of TACACS+ servers, and each server may be configured to handle any combination of authentication, session authorization, command authorization, session accounting, and command accounting.
Note :
- The default network-admin account is exempt from all TACACS+ integration as a fail-safe account for sites without TACACS+ and also to allow access to Pluribus Networks facilities if TACACS+ is unavailable or unreachable. The admin account requires a code from Pluribus Networks Customer Advocacy to login. Because you can access the shell through the CLI, the administrator’s account is rarely needed.
- The Pluribus account password is the same as the network-admin password and when the network-admin password is changed, the Pluribus account password also changes. The login shell for the Pluribus account is nvauditsh and the same can be used to enable auditing for commands run from the admin account. Logins on both types of accounts are disabled if a TACACS+ server with the parameter authen-local is active.
When the TACACS+ server is configured and is working correctly, then the :
- Local users from /etc/passwd or /var/nvOS/etc/*/user_config.xml are not allowed to login
- Authorization and Accounting for shell commands are enabled
- Authorization and Accounting for FRR commands are enabled
- Ability to drop into the shell from the CLI commands are allowed
You can configure TACACS+ by using the aaa-tacacs-create command and then, you can login to the switch and get CLI access using an account configured on the specified TACACS+ server.
The parameter authen-local controls if a TACACS+ server is used to authenticate local accounts or not. Netvisor ONE tracks errors between Netvisor ONE and the TACACS+ server and if a communication error occurs, then local authentication is allowed until communication with the TACACS+ server is recovered. This functionality enables the recovery of the system during an issue in the TACACS+ server. To allow a local account to authenticate, you must configure all active aaa-tacacs instances with no-authen-local option.
Local accounts include the accounts configured using the commands, user-create and user-modify, and the accounts such as admin and pluribus. Logins for both types of accounts are disabled if a TACACS+ server is set with authen-local as active.
The vtysh command is used to configure FRR for authorization and accounting of FRR commands.
The authentication protocols supported for TACACS+ are:
- PAP
- CHAP
- MS-CHAP
Figure 13-1 illustrates a simple TACACS+ implementation.
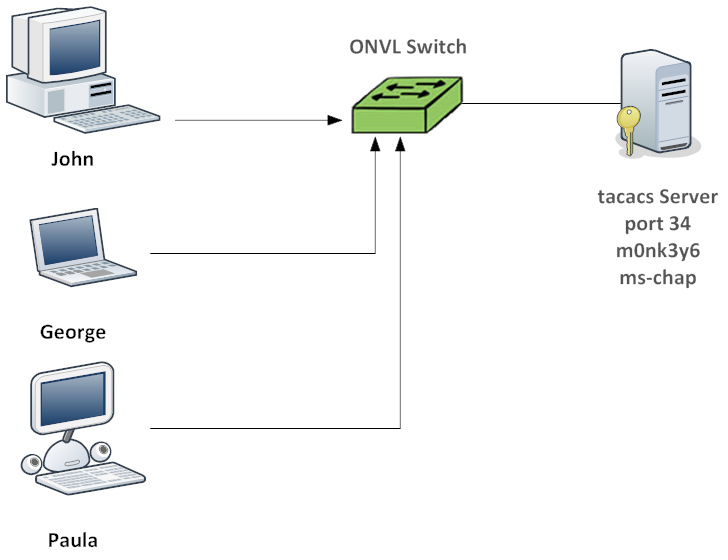
Figure 15-1: TACACS+ Implementation
