
Using vFlow to Analyze Packets in Real Time
On Netvisor ONE switches, you can capture one or multiple traffic flows, either on a specific switch or across the entire fabric using the scope option. To do that, you can leverage the vFlow functionality (refer to the Configuring and Using vFlows chapter for more details).
For example, you can create two vFlow policies to capture traffic bi-directionally between two endpoints (from server 2.2.2.2 to client 2.2.2.3, and vice versa) like so:
CLI (network-admin@switch) > vflow-create name srvclient scope local src-ip 2.2.2.2 dst-ip 2.2.2.3 action copy-to-cpu log-packets
CLI (network-admin@switch) > vflow-create name clientsrv scope local src-ip 2.2.2.3 dst-ip 2.2.2.2 action copy-to-cpu log-packets
To analyze the captured traffic, you can start a new CLI session and run the vflow-snoop command. (To stop vflow-snoop, press CTRL+C within the CLI session.)
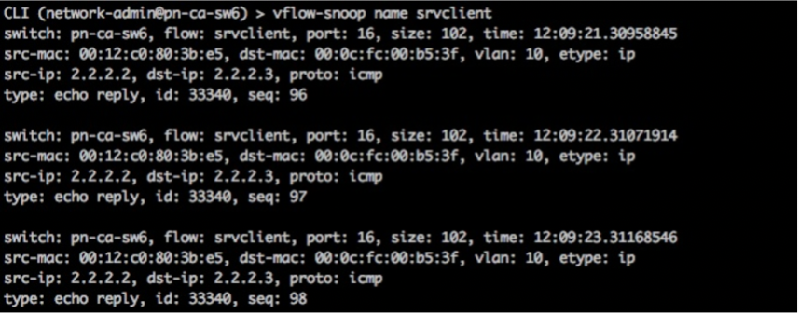
To display the information of the packets sent from server to client, run the command:
CLI (network-admin@switch) > vflow-snoop name srvclient
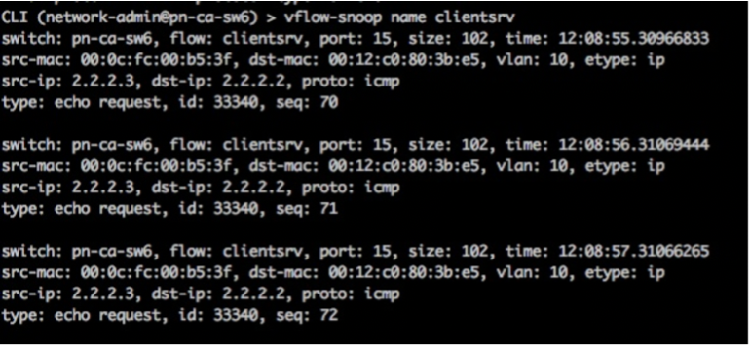
In the same session or in a separate one, to display the information of the packets sent from client to server, run the command:
CLI (network-admin@switch) > vflow-snoop name clientsrv
In addition, you can use the vflow-snoop command with the log-packets option to send packets to an associated pcap file, for example on all the fabric nodes like so:
CLI (network-admin@switch) > vflow-snoop scope fabric src-ip 112.168.3.105 action copy-to-cpu log-packets
Live capture continues until the packet capture file is rotated. By default, the maximum packet capture file size is 10MB but it is configurable with the packet-log-max option of the vflow-create and vflow-modify commands.
Note: The log-packets feature is supported only on the Pluribus Freedom F64-M, F64-L/XL/FL1T and E28Q-L switches.
You can then use the Wireshark software (www.wireshark.org) or other tools to interactively analyze packets that are captured with the above option: that is, you can copy the pcap file to the host running Wireshark to analyze the traffic.
