
Configuring Remote Port Mirroring
Configuring VLAN-based Remote Port Mirroring
Remote port mirroring copies traffic between different switches and the mirrored traffic is carried over a specified VLAN. This functionality is also known as RSPAN.
Take for example, the topology below:
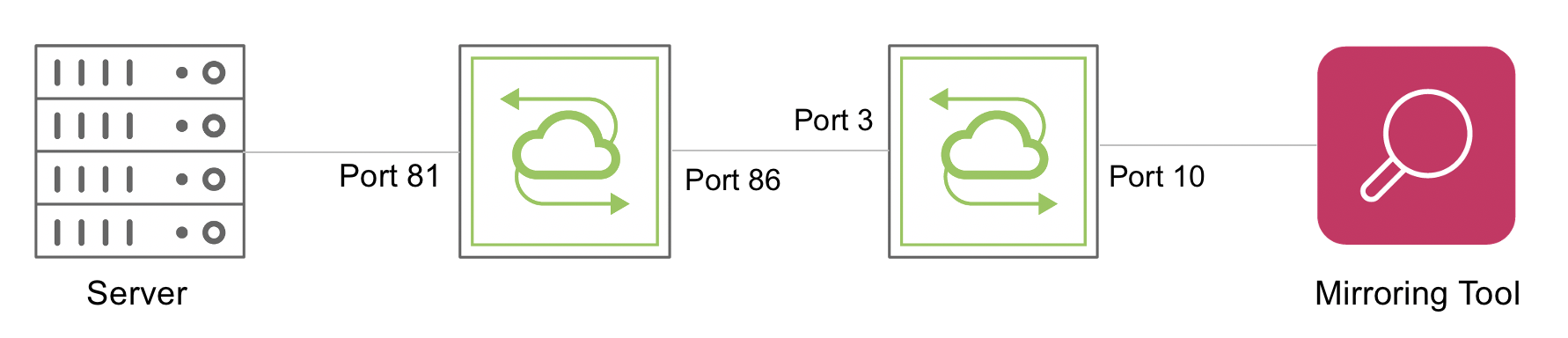
Figure 11-5: VLAN-based Remote Port Mirroring Topology
To configure remote port mirroring over a VLAN, you must first create a mirror instance on the source switch (switch1). You must also specify over-vlan as encapsulation scheme. For example:
CLI (network-admin@switch1) > mirror-create name mirror33 direction ingress in-port 81 out-port 86 other-egress-out allow span-encap over-vlan span-tagging-vlan 200
Use the mirror-show command to view the configuration:
CLI (network-admin@switch1) > mirror-show
name: mirror33
direction: ingress
out-port: 86
in-port: 81
filtering: port
enable: yes
other-egress-out: allow
span-encap: over-vlan
span-tagging-vlan: 200
nvie-mirror: false
This command tags all ingress packets on port 81 with VLAN 200 and these packets are sent out on port 86. If VLAN 200 is not configured on switch2, the packets are dropped at port 3. Thus, VLAN 200 must be configured on port 3 and port 10 of switch2.
CLI (network-admin@switch2) > vlan-create id 200 scope local ports 3,10
The alternate method is to configure a mirror on switch2 with a VLAN 200 tagging.
For example:
CLI (network-admin@switch2) > mirror-create name mirror35 in-port 3 out-port 10 span-encap over-vlan span-tagging-vlan 200
Use the mirror-show command to view the configuration:
CLI (network-admin@switch2) > mirror-show
name: mirror35
direction: ingress
out-port: 10
in-port: 3
filtering: port
enable: yes
other-egress-out: prevent
span-encap: over-vlan
span-tagging-vlan: 200
nvie-mirror: false
With this configuration, the mirrored packets can be analyzed at port 10 of switch2 by using a packet analyzer tool.
Note: If the path for the mirrored packets to reach the destination include multiple switches, the SPAN tagging VLAN must be configured on all the intermediate switches.
Configuring IP-based Remote Port Mirroring
Remote port mirroring can be configured to send packets to a destination reachable over Layer 3. This is achieved by encapsulating mirrored packets with an L3 header so that the packets can be routed. This functionality is also known as ERSPAN.
Consider for example, the topology below:
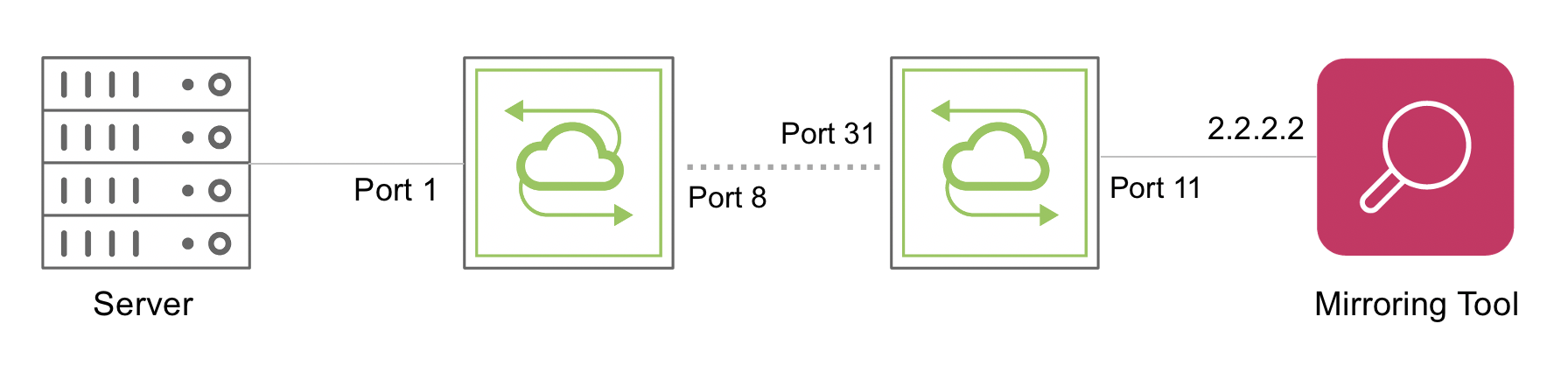
Figure 11-6 - IP-based Remote Port Mirroring Topology
To create a mirror over IP configuration, you must specify over-ip as encapsulation scheme.
For example:
CLI (network-admin@switch1) > mirror-create name mirror37 in-port 1 out-port 8 span-encap over-ip span-local-ip 1.1.1.1 span-remote-ip 2.2.2.2 span-src-mac 33:44:55:66:77:88 span-dst-mac 99:aa:bb:cc:dd:ee other-egress-out allow
To view the configuration, use the mirror-show command:
CLI (network-admin@switch1) > mirror-show layout vertical
switch: switch1
name: mirror37
direction: ingress
out-port: 8
in-port: 1
filtering: port
enable: yes
other-egress-out: allow
span-encap: over-ip
span-local-ip: 1.1.1.1
span-remote-ip: 2.2.2.2
span-src-mac: 33:44:55:66:77:88
span-dst-mac: 99:aa:bb:cc:dd:ee
span-tos: 0
nvie-mirror: false
Note that the IP-based configuration has local and remote IP addresses and MAC addresses explicitly specified. VLAN tagging and ToS setting are optional parameters.
- span-local-ip and span-src-mac can be specified as the router IP and MAC addresses of the local switch on which the mirror is created.
- span-remote-ip must be the IP address of the packet analyzer tool.
- span-dst-mac must be the next-hop MAC address.
- other-egress-out allow must be configured as the L3 protocol fails to come up otherwise.
- out-port must be the egress port to reach the next-hop IP address.
Note: The local router should have a route to reach the packet analyzer's IP address.
