
Corporate AD / LDAP Server
Corporate AD / LDAP Server
There are features and functions used in Arista NetVisor UNUM and Insight Analytics that are common throughout the user interface (UI). Please refer to the Common Functions section for more information on the use of these functions and features.
The following example details connecting NetVisor UNUM to an corporate AD / LDAP Windows Server.
Prerequisites
To configure NetVisor UNUM to use LDAP, you need the following information in advance.
•Type – Type of Authentication Service used on the domain, either LDAP, AD or, possibly both.
•Server URL – The LDAP server or service provider name and type of connection supported, either LDAPS (secure) or LDAP (non-secure), and the port numbers assigned to these servers, typically 636 and 389, respectively. When accessing a Windows Active Directory (AD) enabled server running LDAP services, some LDAP configurations may use alternate ports such as 50000 and 50001 for LDAP (non-secure) or LDAPS (secure). Check with your AD Administrator for specific port assignment information and if required.
•Base DN – The name of the base organization and domain name.
•Manager DN (Distinguished Name) – The distinguished name (DN) used for the LDAP manager. This name is the account with admin-level privileges and allowed access to the LDAP server or service provider. This may exist as a UID (User ID) or a CN (Common Name). A Manager DN account name must be a binding user within the LDAP service.
•Manager Password – The password for the admin-level account.
•User DN Patterns – DN patterns used for simple bind authentication. These are the groups where user accounts exist.
•User Search Filter – Any search filters. Specific filters used by your LDAP server, Service Provider or Windows Server.
LDAP Server Settings
Example Settings
Type: LDAP
Server URL: win-2019-kp (or the IP address) on Port 389
Base DN: CN=Users,DC=radiowindermere,DC=com
Manager DN: CN=cool streams,CN=users,DC=radiowindermere,DC=com
Password: <password>
User DN Pattern: uid={0},cn=Users
User Search Filter: (&(objectClass=top)(sAMAccountName={0}))
Usage Note:
After the initial configuration phase, you can test the connection using the built-in NetVisor UNUM test feature. However, this is only a pass/fail test and does not provide any troubleshooting information.
Arista Networks recommends using a third-party LDAP tool or OS commands to access and view the LDAP server or service provider to review the structure and required parameters.
Corporate AD / LDAP Server
OS Commands
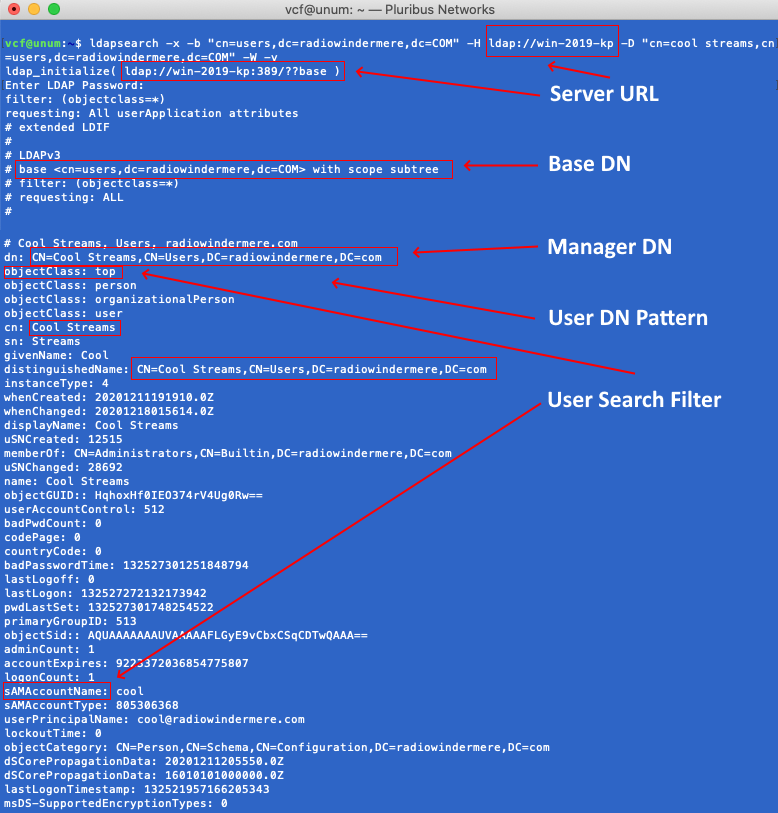
In the following example, running the ldapsearch command on Linux or macOS returns useful information regarding the LDAP service structure.
|
ldapsearch -x -b "cn=users,dc=radiowindermere,dc=COM" -H ldap://10.0.1.229 -D "cn=cool streams,cn=users,dc=radiowindermere,dc=COM" -W -v |
Command Syntax
•-H - LDAP URL
•-x - Simple Authentication
•-b - Base DN or Search Base starting point.
•cn - Common Name
•ou - Organizational Unit
•o - Organization Account
•dc - domain specifics
•-D - Manager DN
•-W - Prompt for password
•-v - Verbose, provides additional information.
Note: To view detailed information regarding the ldapsearch command use the following command:
|
man ldapsearch |
After entering the above command string and, if the connection is successful, enter the password associated with the account bound to the service.
In this example, the administrator-level account is: cool streams
You should receive a prompt to enter the password, or if you receive an error message, you will need to re-verify the LDAP settings.
A successful login displays information, as illustrated in the following example, which provides much more information about the Windows Active Directory and LDAP contents.
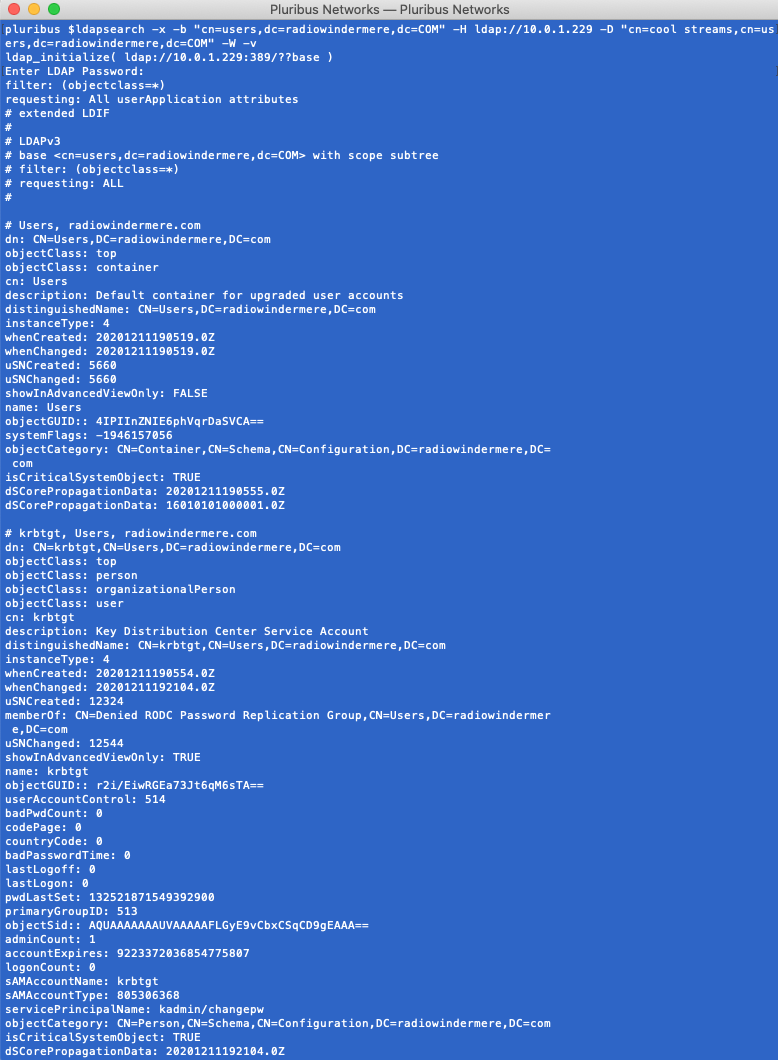
The data presented corresponds to the Windows AD information presented on the Windows Server.
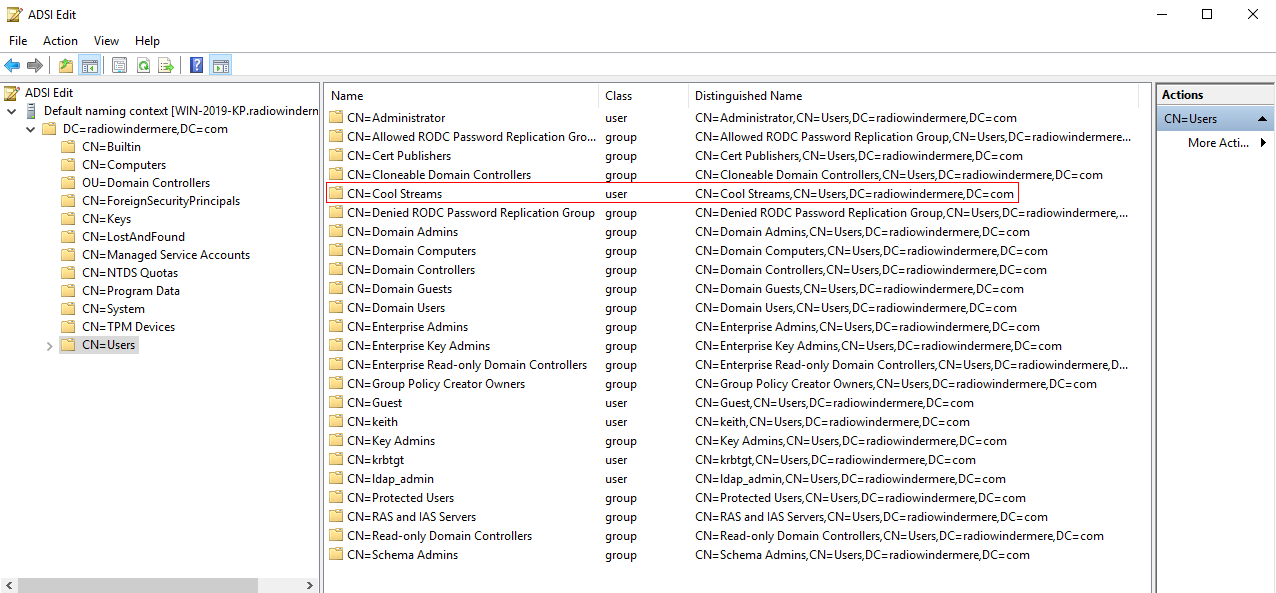
NetVisor UNUM LDAP Configuration
After confirming the login settings proceed to add the LDAP server or service provider to NetVisor UNUM selecting Menu Bar → ![]() → Auth Server from NetVisor UNUM.
→ Auth Server from NetVisor UNUM.
The following dashboard displays when first configuring an Authentication Server if no previous servers exist.
Add Authentication Server
Click the Add Auth Server button to begin.
Enter the information for your server or service provider.
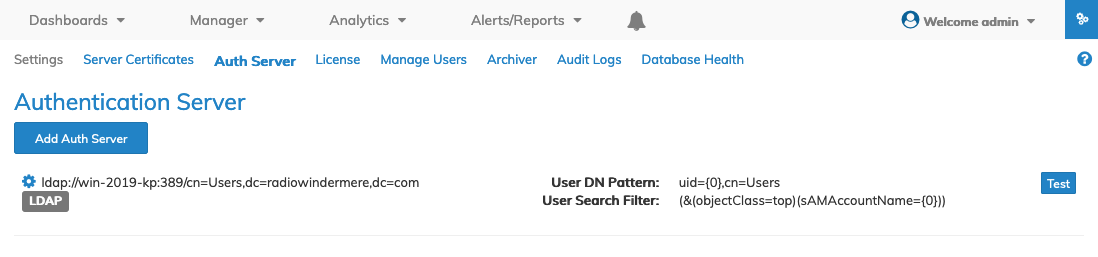
Example Information
Server URL = Type, Server Name and Port
Type = LDAP
Hostname = win-2019-kp (or IP address)
Port = 389 (using a non secure ldap connection)
Base DN = cn=Users,dc=radiowindermere,dc=com
Manager DN = cn=cool streams,cn=Users,dc=radiowindermere,dc=com
Password = <password> ldap_password associated with the Manager DN account
User DN Pattern = uid={0},cn=Users
User Search Filter = (&(objectClass=top)(sAMAccountName={0}))
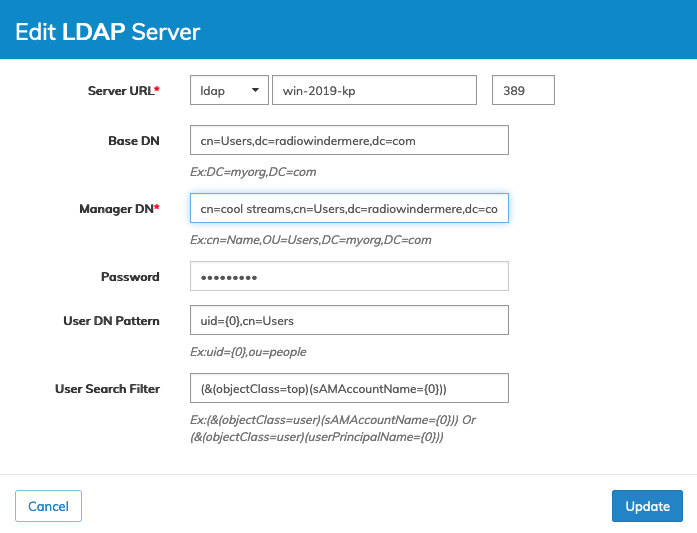
These entries align with the ldapsearch data obtained from the command output.
|
ldapsearch -x -b "cn=users,dc=radiowindermere,dc=COM" -H ldap://win-2019-kp -D "cn=cool streams,cn=users,dc=radiowindermere,dc=COM" -W -v |
After entering the settings, click Update, and the LDAP Service displays in the dashboard.
Enter an LDAP user account name and the associated password and click Test.
Arista Networks recommends testing with an admin-level account initially. However, any qualified LDAP user account is acceptable for testing purposes.
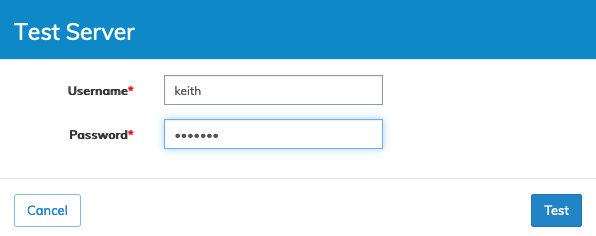
Enter the LDAP user name and associated password and click Test.
NetVisor UNUM returns a Success or Fail message.
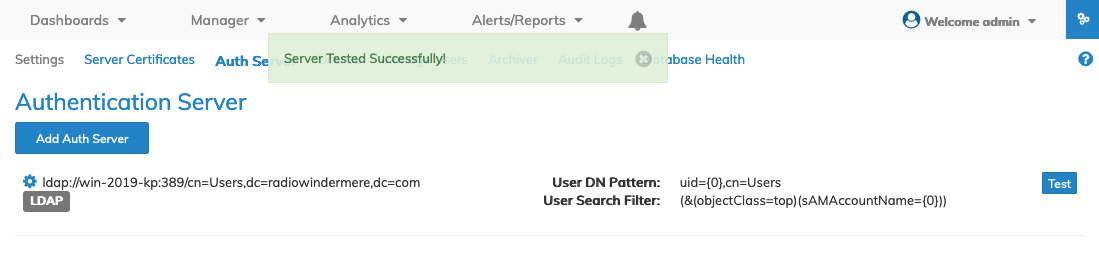
If the selected user name does not exist or the password is incorrect, NetVisor UNUM returns a "failed" message.
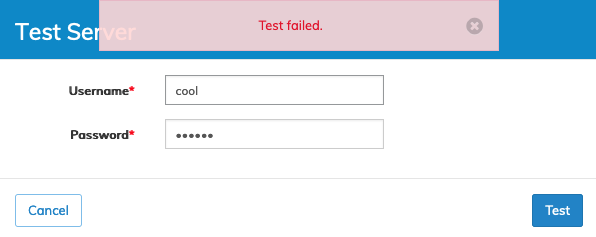
As previously stated, this is only a pass/fail test, which does not provide any troubleshooting information.
If you encounter a failure, try re-entering the user name and password.
The ldapsearch command, described above, provides useful information to aid in troubleshooting.
Note:
|
1) |
If the test fails, carefully review all settings. |
|
2) |
Verify the Server name is resolvable. Use the IP address in place of the Server name. |
|
3) |
If using the IP address works, verify the DNS settings and ping the server using the FQDN. |
Edit LDAP Settings
Use the Cog ![]() icon and select Edit to make changes to the LDAP Server settings.
icon and select Edit to make changes to the LDAP Server settings.
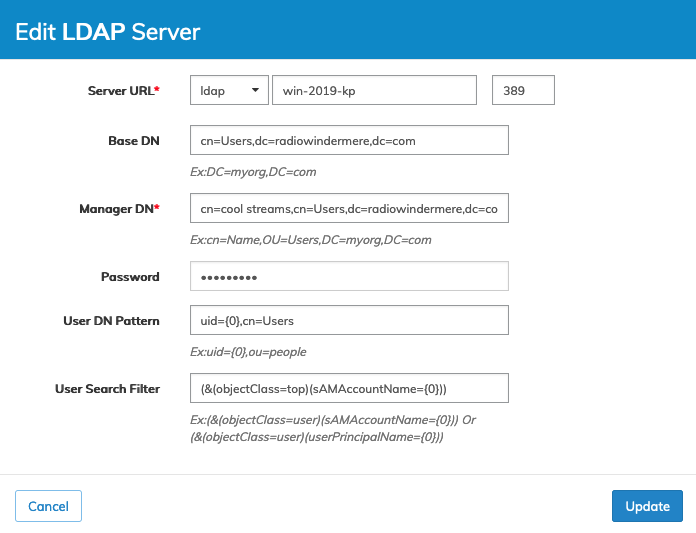
Click Update to save the revised settings.
Logging in to NetVisor UNUM
After LDAP account verification is successful, login into NetVisor UNUM using LDAP credentials. In the following example, "cool" is the LDAP user name.
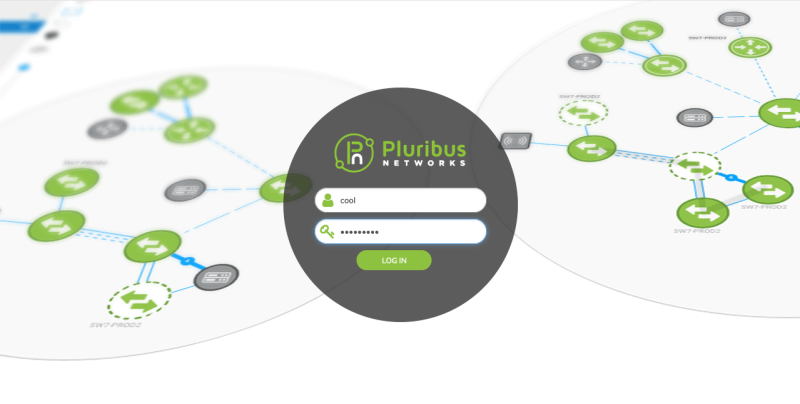
Once logged into NetVisor UNUM, the LDAP user is assigned a User Role and can view NetVisor UNUM dashboards.
Note the LDAP user name (illustrated in red for example purposes).
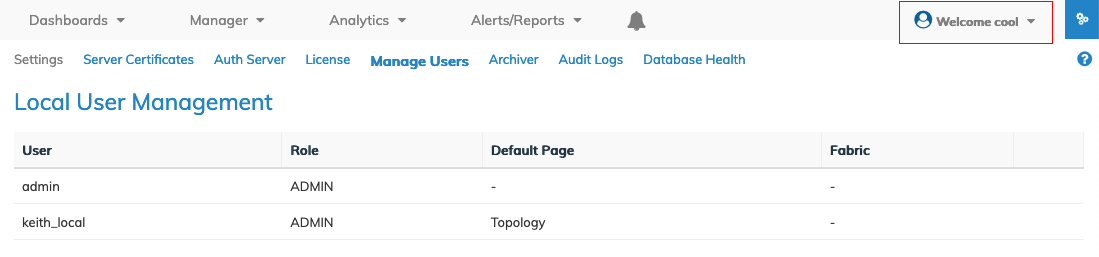
Note: NetVisor UNUM assigns an LDAP account to a User Role, and they do not appear in the Local User Management dashboard.
LDAP User Roles:
NetVisor UNUM currently supports two roles, User and Local Admin. NetVisor UNUM assigns all LDAP or AD users to the User Role in NetVisor UNUM.
NetVisor UNUM ignores any assigned LDAP or AD roles.
Please refer to Manage Users for more information about these roles.
Troubleshooting Tools
There are numerous tools to aid in troubleshooting LDAP connectivity problems.
However, first and foremost, verify all settings are correct and match your LDAP Service Provider or AD/LDAP Server requirements.
Some of the tools that exist include:
OS Tools
•LDAPSEARCH - Unix, Linux, macOS
•TCPDump - Unix, Linux, macOS
Windows Tools
•LDP.EXE
•Active Directory Explorer
•Active Directory Users and Computers
Third-Party Tools
•LDAP Admin (UI-based tool)
•TCPDUMP for Windows
The above is not an exhaustive list and only intended to provide you with several options readily available to assist in troubleshooting LDAP connectivity issues.
